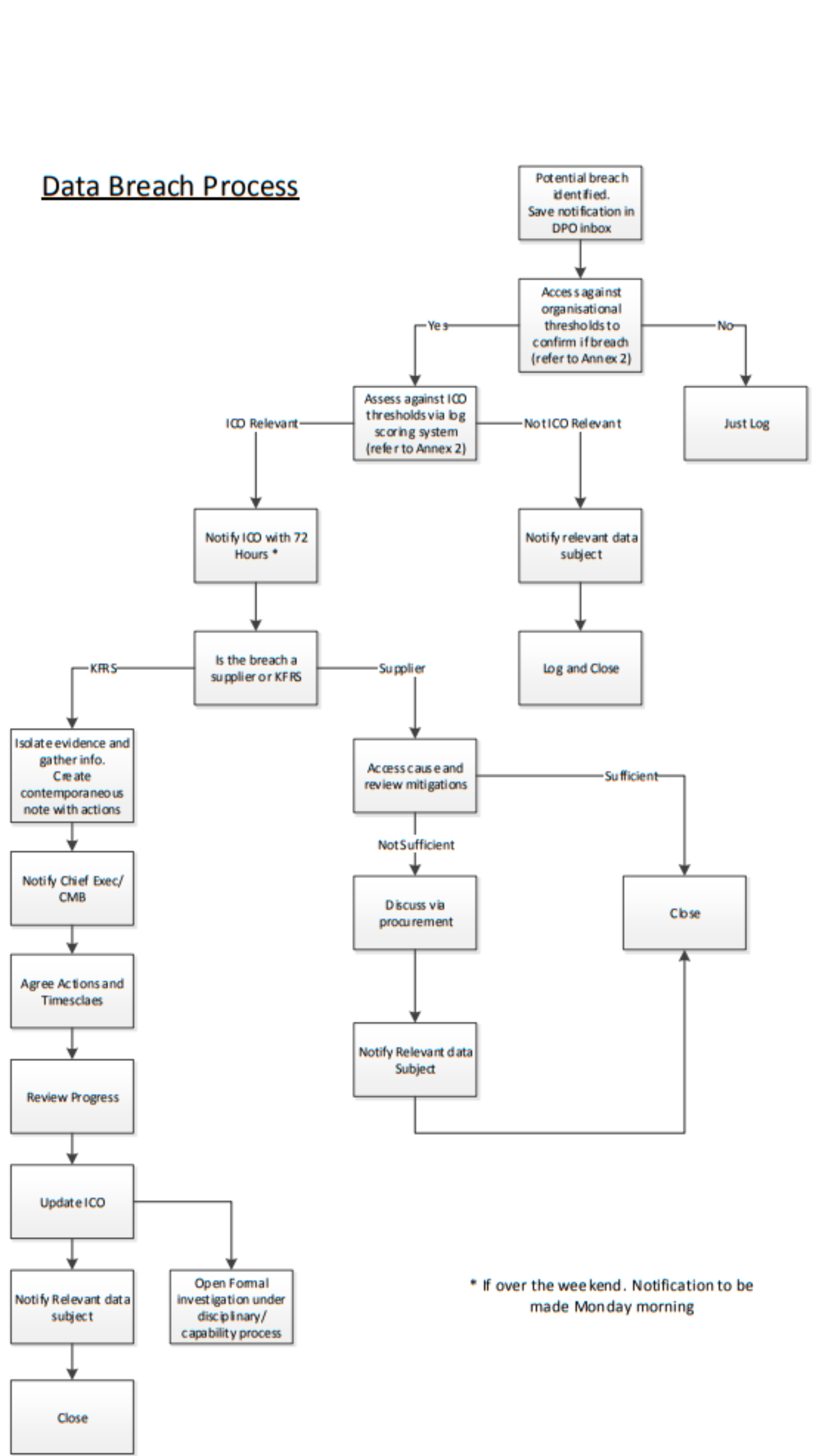
Annex 1: Breach process
The flowchart below sets out a broad overview of how the Authority will respond to a potential data breach or security incident, (regardless of if it involves personal or non-personal data), and subsequently investigate it. Depending on the nature of the potential breach, other processes may also become relevant, such as fault reporting to Information Technology or invoking major incident plans.
Annex two gives some guidance to help in reporting the potential breach. In any case a risk assessment will need to be completed which recognises the volume, sensitivity, impact on individuals rights, organisational impacts and trust and confidence in the Authority of the public and its partners in assessing the severity of the breach.
For the purposes of this Policy a potential breach is defined as:
“The loss, misuse, inability to access, corruption or unauthorised access or disclosure to a data record or records, held on
- the Authority’s Information Technology network (including cloud based services)
- the Information Technology network of one of its suppliers,
- held in paper form,
- held on removable devices.
In line with European Union General Data Protection Regulation Working Party guidance, whilst all personal data breaches are security incidents, not all security incidents are necessarily personal data breaches. Therefore a breach does not need to involve personal data to be considered under this definition”